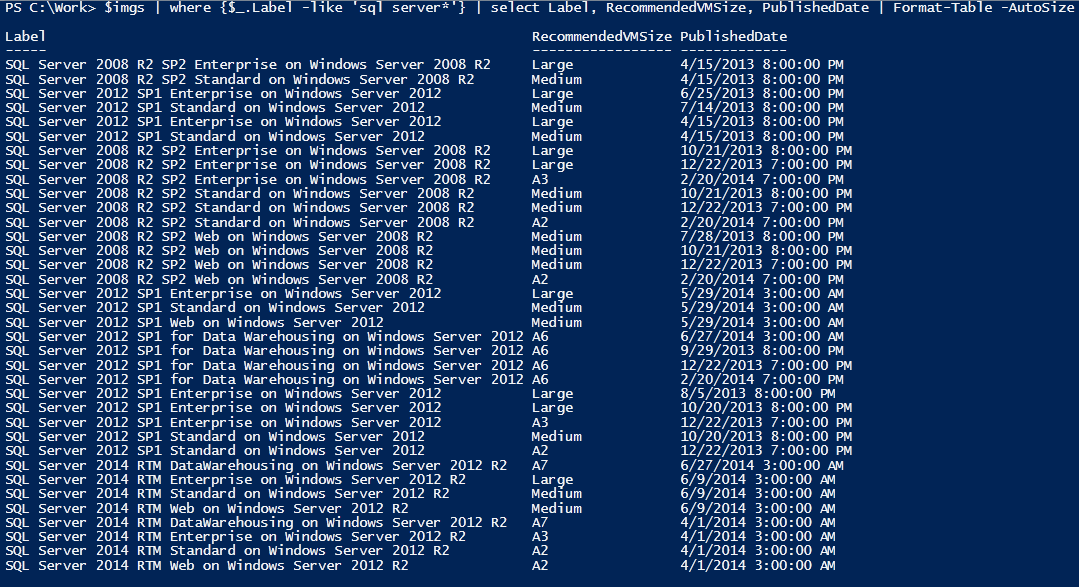
A pretty simple one but something that seems to stump a lot of people. Much of the guidance around connecting to Azure AD suggests you do the following, :
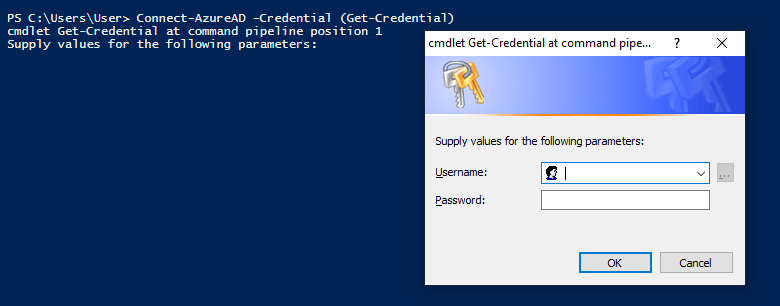
Connect-AzureAD -Credential (Get-Credential)Which is fine for accounts without MFA but lets break this down and we can see why it wont work for accounts with MFA.
- 'Connect-AzureAD' - A function that is part of the Azure AD module.
- '-credential' - An argument passed to the previous command.
- '(Get-Credential)' - The value we are passing is the result of the 'Get-Credential' function. This function only has the ability to collect username and password
So we can see that 'Get-Credential' is the problem, and if we run that command we can see it in action.
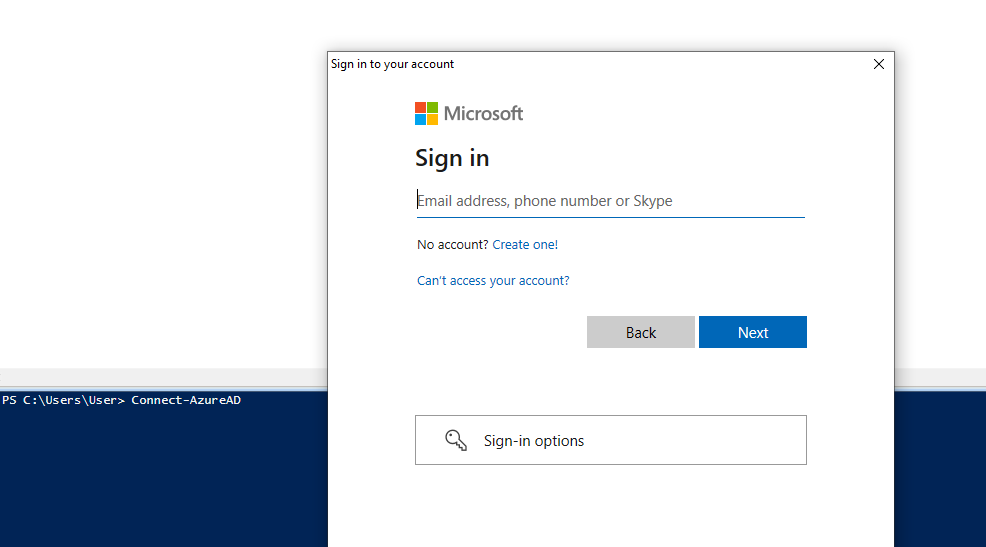
So how do we get passed this if we are trying to log in via a MFA user? Well its much more simple that you would expect.
Connect-AzureADThe same command without any arguments will prompt the M365 login page your are probably familiar with and will take you via your choses MFA method automatically.
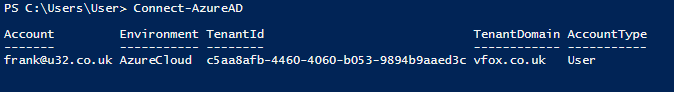
Once you have negotiated authentication you will get the familiar summary of your current session.
This is all good and well if you are directly working on something but how would you do this in a scheduled script? Well that dear readers will the subject of another article.