
If you have any device that has an exernal IP the chances are you are used to see attempt after attempt of various alien IP address's trying to login to it.
This is the system log from one of the fortinets I have deployed in the world
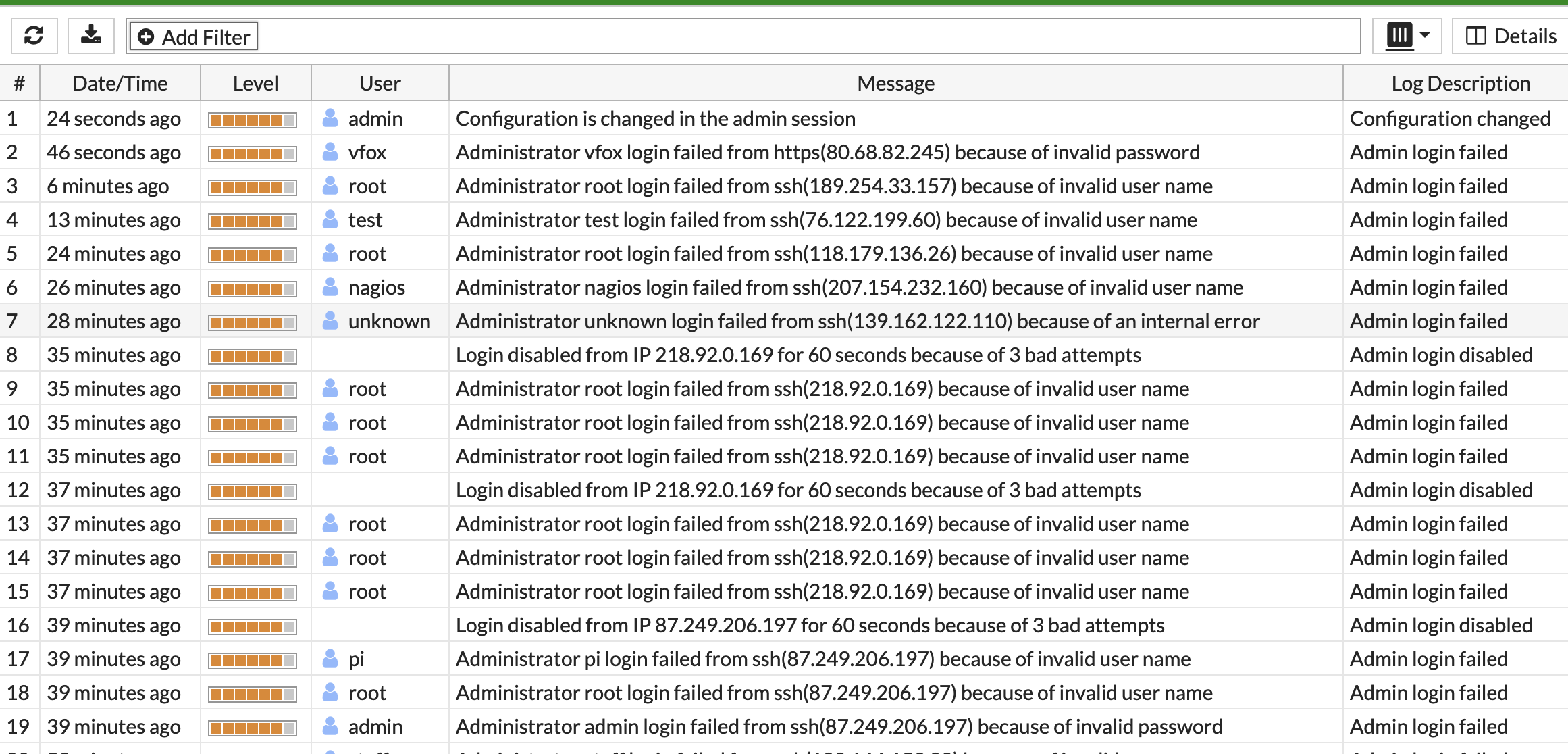
As you can see, lots of annoyoing login attempts. After 3 the fortinet will block the IP from making any more attempts for 60 seconds. Unfortunatly this will do little to prevent the attacker from persisting.
If you have been sensible enough to disable the default admin accounts (Admin/root etc), and use a strong password this IP block will more than likley stop intruders from getting in, but it would be nice if they wern't constanty filling up you logs. The best thing to do would be to restrict admin logins to known IP ranges but that isn't always possible. So a good option is to extend the IP lockout from 60 seconds to at least 5 minutes. I have found that 5 minutes is enough to make most attackers move on and leave you alone, but the longer the better. Just remember that if you type the password incorrectly 3 times you will also be locked out for this period.
Here is how to do it :
From the command line
config system global
set admin-lockout-duration 600
end
Very simple and very effective.
You may also wish to combine this with an increase in login attemps before a lockout. 10 would still be safe.
config system global
set admin-lockout-threshold 10
end
If you manage 10 typo's in a row, frankly you deserve to be locked out..